Hello Guys !! Hope the new year started good for you all. Continuing my previous statement of “sometimes functionality leads to vulnerability..”, I am gonna start discussing this another feature of the browser which can lead to leaking sensitive information like your passwords and sometimes even you complete Credit Card details. Definitely there are scenarios and certain dependencies which we will go throug h in later in the post.
h in later in the post.
What Actually this vulnerability is !!
As you have already noticed the back and forward buttons of the browsers. These buttons simply navigate you to through the pages you have visited during your browsing history. So definitely browsers have the ability to maintain a recent record of pages that a users visits during the session. The back and forward button on browsers use this functionality to display the pages recently browsed.
In addition browsers also keep track of variables that were sent to server(Even by a POST Request) while you fetched any page.
These attractive feature enhances the user experience definitely but can be very harmful if the applications doesn’t handle it properly.
How it happens and How we can find it ?
Lets suppose there is a website called https://testsite.com and the login page URL is https://testsite.com/login. Once the user is gives his credentials it redirects to https://testsite.com/home. Then he browses through the Website internal pages, do some transactions and then logs out from the application. Now if the user leaves his browser as it is after logging out and works on a shared machine and some other guy has an access to that machine(This is the only condition to exploit this bug that the attacker needs the physical access of the open browser after the logout action was performed by the victim.)
The attacker can use the back button to crawl through the pages the victim has visited lately. Please note he can not make any changes anywhere as it’s not an active session(although, some applications will even allow him to do that.). While crawling through if he notices any document expired error page like below, it means there may be some chance to get some information.
Now here the attacker will use another browser feature “Refresh”, but before doing that he will configure a HTTP proxy tool like burpsuite, ZAP etc to make sure he captures the request going from the browser to the server. Once he refreshes, the browser will ask the confirmation to resend the information to the server and the information will be captured in the proxy tool. Such kind of bug can be very harmful if it happens after Authentication, registering the user, changing the password, Payment gateways etc. where the user has submitted any sensitive data to the server.
Why it happens ?
As a part of functionality browser instance remembers the pages that it had displayed to the user.It also keeps track of all requests that were sent to the server for fetching a particular page. In the above case the “https://testsite.com/home” was displayed only after the user had entered his Credentials(ID+Password). So the browser remembers the request that was sent for fetching the home page. – which contains the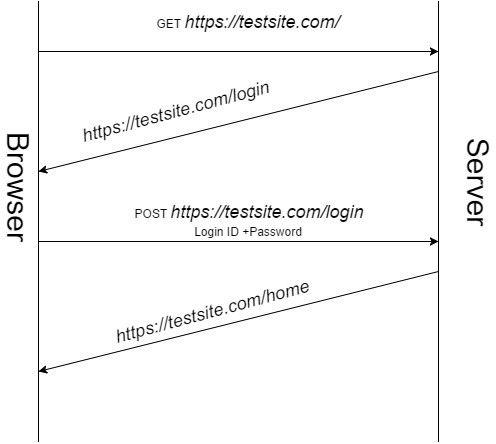 “Login ID” and “Password” the user had provided on the login page. Now when the attacker tries to refresh button on home page, the request that had been used to render the home page is resent to the server. This request contains the credentials which the Attacker will intercept.
“Login ID” and “Password” the user had provided on the login page. Now when the attacker tries to refresh button on home page, the request that had been used to render the home page is resent to the server. This request contains the credentials which the Attacker will intercept.
Below image will describe how an application is programmed insecurely allowing such attack to happen.
This is quite simple authentication request flow, so the back button will directly take you to the previous pages(expired one also) without any second level of check.
How to fix it ?
Just assume about a redirect page in between the authentication pages (or any other session changing step, even lets say payment gateways).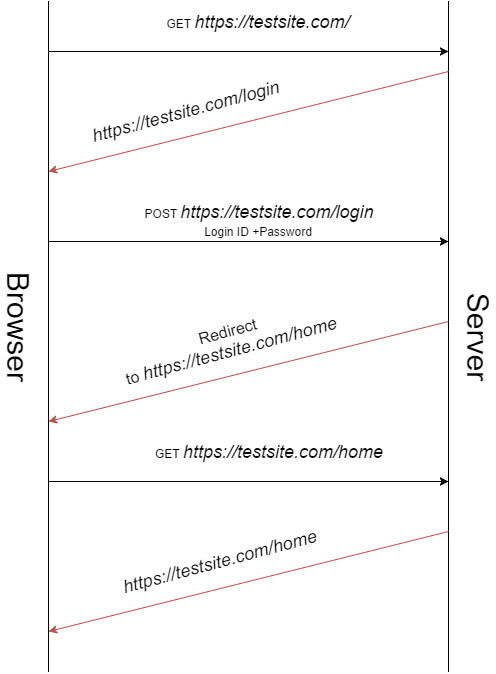
In this case the user submits the Login ID and password and redirects to another page internally, Here the redirection page doesn’t display on the browser, hence there is no possibility of the attacker to unset he back button to reach the page. Here an important note is that the redirection request must contain the session ID assigned to the user after authentication.
Back Refresh Attack on Qualys Scanner Portal
I was actually lucky to find this bug in QualysGuard. Being a licensed user for one of their product, It got late while renewing the product. When I tried to log in to the application it presented me the following error.
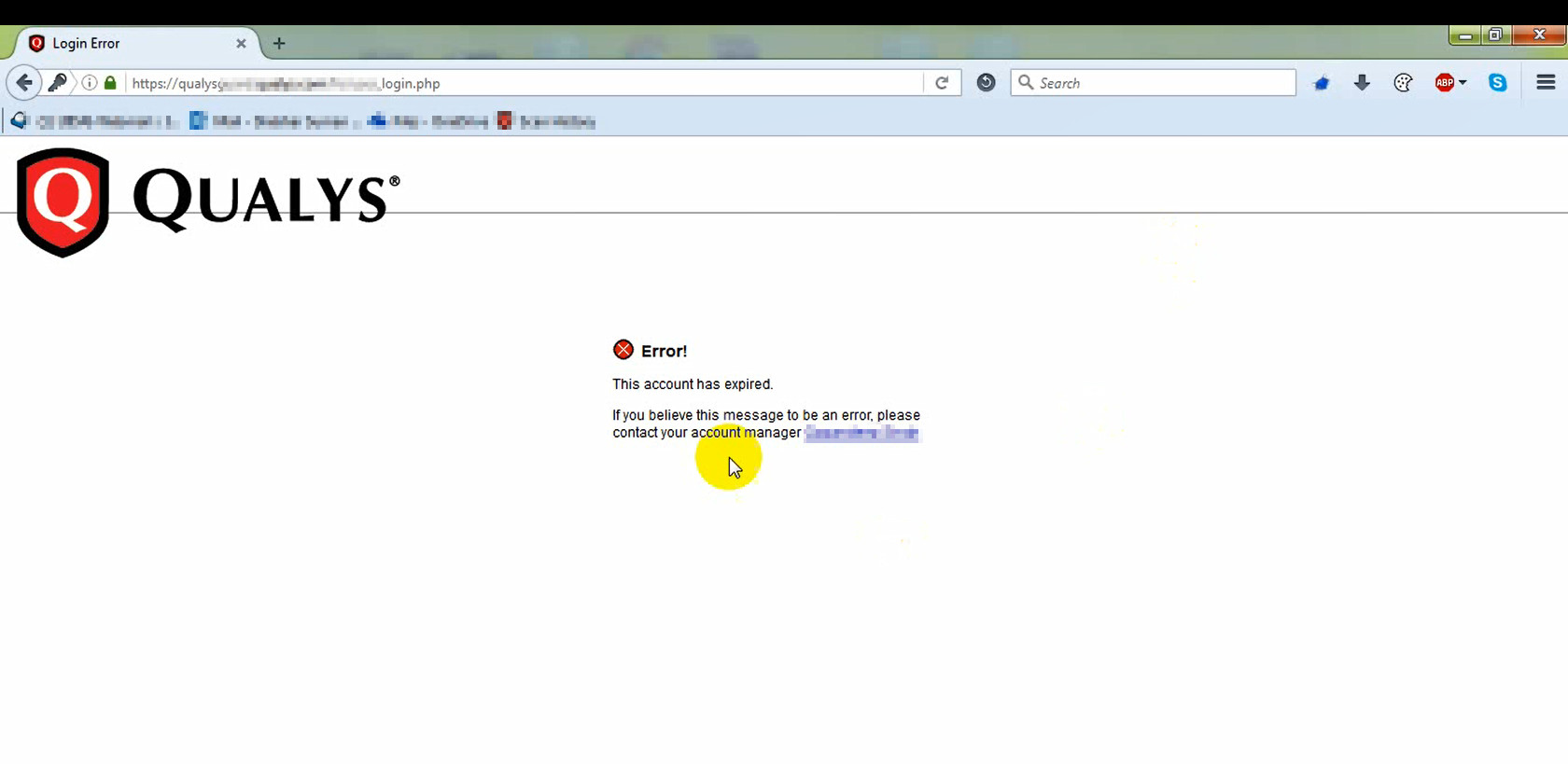
I observed there is no logout button anywhere on the page when I tried to capture this in burp. It made me sure about no redirection after login as well because logically the login was not successful due to my license expiration.
Then I thought to play around with back and forward buttons. After one back and one forward button it gave me the page expiration page. It confirmed that the browser will try to resubmit some data again.
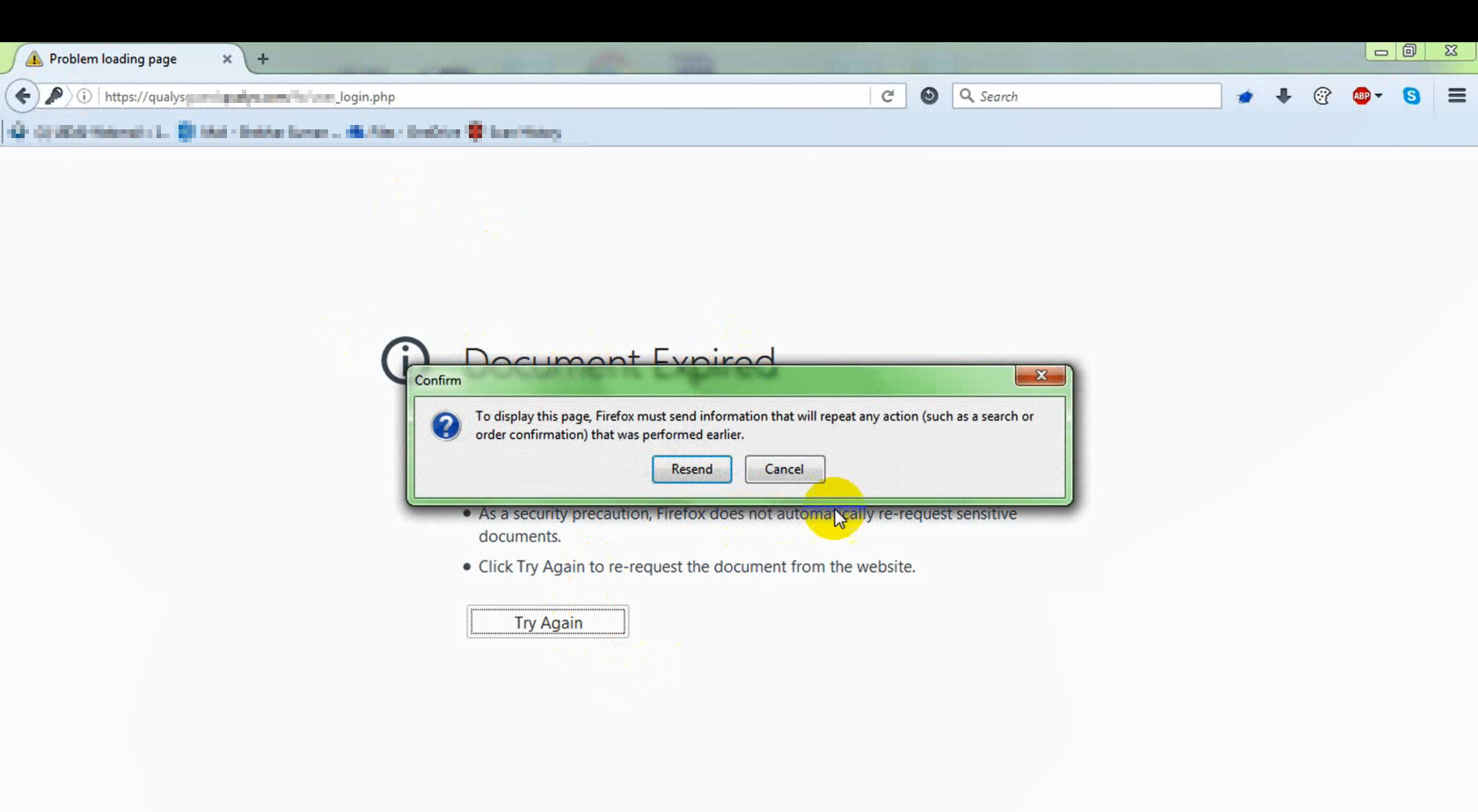
I resubmitted the data again and captured it in burpsuite and Bingo !! it resubmitted my credentials.

Timelines for the bounty
It took me a while to convince QualysGuard team about this vulnerability. It’s quite clear as this bug requires an attacker to have physical access of the machine.
Also at one instance they thought that it’s not a risk as they have implemented HTTPS. I then provided all those write ups I found about this bug over the Internet. Finally they have accepted and implemented the fix.
26/05/2016 :- First report of the vulnerability
31/05/2016 :- Denied this as a bug as they have implemented SSL
01/06/2016 :- Provided them more Information about the vulnerability
01/06/2016 :- Denied again saying it requires MITM attack to happen and with SSL it’s highly impossible
03/06/2016 :- Provided them better understanding of the vulnerability that this a browser based attack. I also asked for public disclosure if this they don’t consider as a valid bug
03/06/2016 :- They have accepted this a valid bug and promised a fix
14/10/2016 :- After continues follow ups, Qualys team finally implemented the fix and asked me for the confirmation.
16/10/2016 :- I confirmed the fix.
23/10/2016 :- Bounty and Swag received.
Great write up..
Google lists this on number 5 for search in back refresh attack. But I think this is the best write up I have read on Back Refresh attack.
And congrats for the bounty.